XtraAccess 1.20
Released 24 years ago. April 2001
Copyright © MegaSecurity
By Watchdog
Informations
| Author | Watchdog |
| Family | XtraAccess |
| Category | Remote Access |
| Version | XtraAccess 1.20 |
| Released Date | Apr 2001, 24 years ago. |
| Language | C++, compressed with UPX |
Additional Information
Server:
C:\WINDOWS\ISPDLL32.EXE
size: 301.568 bytes
port: 45100 TCP
startup:
HKLM\Software\Microsoft\Windows\CurrentVersion\Run
Author Information / Description
"XtraAccess V1.02 Client/Server software"
XtraAccess version 1.02
Welcome to Xtra Access, a remote control program to allow you access and
control of multiple pc's from a distance via the Internet.
So exactly WHAT is Xtra Access ?, is it a remote administration program,
a trojan horse, a virus even ?
Xtra access consists of two files, one is the client,
which is basically the GUI (user interface or control panel), the other is the server,
which is the remote program that run's on the distant machine and
listens / executes commands sent to it via the client,
in normal use it is a very handy instrument,
which I myself use a few times a week consistently in conjunction with
RCM2000 to gain access to technical files on the workshop computer.
Xtra access is a REMOTE ADMINISTRATION TOOL,
but it can also be used in STEALTH MODE which then makes it a TROJAN HORSE,
this has a wide meaning in the computer world and under the TROJAN HORSE umbrella
it can also be classed as a VIRUS, but it's ability to infect machines does not exist,
and it can only manually infect a computer, and cannot migrate from computer to computer,
therefore the VIRUS title does not apply to this version of REMOTE ADMINISTRATION TOOL.
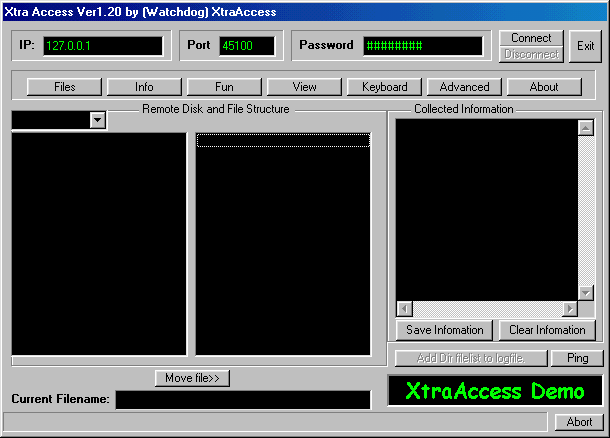
The client has many functions available to control the server,
CLICK HERE to view a list of the available functions.
Using additional modules that will be available shortly,
Xtra Access's functionality can be extended to provide new uses.
SO WHAT CAN XTRA ACCESS BE USED FOR ?
SECURITY:
scenario: your working away from home, you want to check the status on your house
assuming your computer is still there :-)), connect to your computer by dialing
your home telephone number, the computer will answer the phone
(using the bundled RCM2000 program), and then send an e-mail to you with connection details,
RCM2000 will have run the server for you when it connected,
and now you simply connect up to your home machine and view any connected webcam's or camera source.
scenario: view the workplace from home to make sure everything is secure
scenario: you know if employee's are connecting to the web, if they are, where are they going,
and what files are they transferring / downloading ?, if you need to know secretly,
XTRA ACCESS allows this via the STEALTH SERVER.
WORKTOOL:
scenario: Gone home from work and forgot that document you saved, don't worry,
phone up the computer and retrieve it by using Xtra Access's download file options,
even finish the document at home then upload it back to the computer
ready for when you get back to work.
scenario: working at home and need to make sure a file / document is available
to someone in the morning, or straight away ?, open up a chat,
tell them your transferring the file to a specified directory,
then when it's transferred let them know, they can carry on working whilst
chatting to you via the remote chat, or simply leave the file for them to retrieve in the morning.
Scenario: Your searching the web and want to send someone to a webpage,
just enter the URL and they will go there automatically,
chat to them via the remote chat whilst doing this.
Scenario: dual use of XTRA ACCESS: install the server on two machines, one at home, one at work (for example), allow both machines to connect to the corresponding server's, you now have the availability to open up chat window's and view webcam's at the same time, chat to your partner at home, and even listen to them by recording them on the microphone, it's like your own personal pc-pc connection with camera and chat functions. Of course all available XTRA ACCESS functions will be available to both parties, so transferring files etc. can be done two ways.
(please note that it is recommended to use two separate registered version's of XTRA ACCESS for this function because the connection information will only be available to ONE e-mail address, this may require that the second connection information is sent via telephone or e-mail , or via ICQ by one of the parties so that the other can connect. If two seperate server's are running, each party will receive their own connection information).
scenario: kids are connected on their computer upstairs in the bedroom (it's the in-thing nowadays), simply monitor them in the background to make sure they're behaving o the web whilst your downstairs' and can't see what they're doing. Simply grabbing a small desktop capture every few minutes should allow you to keep an eye on their travel's through the web, or even join in with them as you send them to place's you want them to go without you having to 'crowd' their computer in their bedroom, if you don't like the page they're loading, send the 'kick-off-net command, or even shut their computer down completely.
XTRA ACCESS is a MUST-HAVE tool for anyone who works more than one computer, or who has a family of internet user's with multiple internet connections...
THE USES ARE TOO NUMEROUS TO LIST, AND SIMPLY REQUIRES IMAGINATION !
For notification on new modules released for XtraAccess, join mailing list below.
EXTRA ACCESS FUNCTION SUITE (V1.02)
FILE & DIRECTORY
initialize file system (used to command the server to be ready for instructions after connection, some functions require this to be done before execution, such as "Desktop capture and Find File" it is always best to make this command to the server before any others.)
search files (used to search for files of required extension (eg. .jpg / .hex) etc.
reset to c: (used for quick navigation back to root drive)
refresh directory (shows the changes made to a directory)
make directory (makes a directory on one of the available remote pc's drives)
remove directory (deletes a directory)
upload (send a file from the client computer to the remote computer)
download (downloads a file from the remote computer to the client computer)
execute (runs an executable file on the remote computer)
download Cont.. (allows continuation of a previously broken download from the remote computer)
get filesize (shows the size of the selected file on remote computer,
important for estimating download time)
clear file attributes (change the file's properties such as read-only to archive so that it can be deleted)
delete (deletes a file)
rename (renames a file)
edit (real time editing of text / html etc. eg. edit autoexec.bat / win.ini file directly from client)
empty directory (deletes contents of a directory)
VISUAL & AUDIBLE FUNCTIONS
show picture (displays any picture file on remote computer instantly to the remote pc's screen,
either as a picture only, or as desktop wallpaper)
play sound (plays any audio file on the remote computer
(user of remote computer will hear the audio file played provided speakers are connected / switched on)
remote time (displays current time on remote computer)
record microphone (record the sounds received by the remote computer's microphone (bug via the remote pc))
view desktop (view the remote computer's current screen, either quickly (small capture),
or a large detailed view of the screen (full capture),
the quality of the captured picture is adjustable to control download speed)
view webcam (receive streaming video data from any webcam's,
camera's / capture devices connected to the remote computer,
the Xtra Access server automatically searches and informs the client of installed / connected devices).
SENSITIVE INFORMATION
cached passwords (retrieves all available cached passwords used by programs)
get RAS entries (retrieves all dial-up account information,
such as login name and password, and the dial-up tel. number)
email accounts (retrieves all e-mail accounts on remote computer)
ICQ accounts (retrieves all UIN accounts on remote computer)
user name (displays the current computer's username (name of person using the current windows)
machine info (displays various information about the remote computer such as windows version,
system directory etc.)
MISCELLANEOUS FUNCTIONS
mouse (swap / unswap buttons, enable / disable the mouse / set trails on / off)
taskbar (hide / show taskbar)
clock (hide / show the clock)
start button (hide / show the start button)
desktop icons (hide / show desktop icons)
ctrl-alt-del (disable / enable windows ctrl-alt-del shutdown route)
cd-rom (open / close cd-rom draw)
monitor (turn display monitor on / off)
send to URL (display any selected web page to the screen (browser is forced to selected URL))
send question box (pop up a non-closable question box in middle of screen of remote pc,
box can only be closed by inputting data and then clicking 'enter')
remote chat (pop-up a non-closable chat box on the remote computer,
two way communication (same as ICQ message) can then be performed between the client and remote pc),
the chat can only be closed by the client.
keyboard (disable / enable the keyboard of the remote computer)
ADVANCED CONTROL
list open windows (list all currently open windows on the remote computer)
list processes (view the currently running files and program processes,
also allows options for closing / disabling specific files etc.
useful for disabling specific currently running applications)
auto connect(this is used to instuct the remote to re-connect to the internet at a specified time,
this command is aborted if the remote machine is rebooted or switched off and on. )
kick-off-net (immediately disconnects remote computer from the internet)
manual send (send manual control commands to remote server -
trouble-shooting only and at the request of
[email protected]
)
server options (set remote server control properties: change port, change password,
close server (stops server running on remote computer), remove server (de-installs server from the remote computer)
windows (control windows: shutdown, shutdown and re-boot, log off current user)
modules (add functions to Xtra access by installing extra modules, also list currently installed modules)
save information (save displayed information to a log-file)
clear information (clear the current information screen ready for new info)
abort (stop current operation)
move file >> (Removes mis-reported directories to the proper filename window thus allowing command processing)
ping (send a ping to the remote server to check if connection is still active, if yes,
message 'server said pong' is displayed in message bar)
connect / disconnect (enables connection / disconnection between the client and the remote computer)
ip (enter ip of remote computer (this is the address of the computer and is required for connection)
port (this is the communication port used by the server on the remote computer,
the client must be set to the same)
password (for secure access to the server on the remote computer,
the server only allows connection if the password is correct from the connecting client,
this is to secure that only authorized connections are allowed)
IMPORTANT INFORMATION REGARDING XTRA ACCESS SERVER
STANDARD SERVER
The Xtra Access server is always supplied with the following filename: xtraserv.exe
This is a stand-alone executable file that when clicked on and run will pop-up a
small indication showing that the server is running, here is a picture of the bar:
This is known as the 'standard server', and is used in this manner when it is
not a problem for the running server to be visibly noticed.
Use this version of server when running RCM 2000,
this will allow RCM 2000 to answer the telephone and then execute the server
file and thus run a visible server on the computer,
no changes to the registry are made in any way when the server is run from this filename.
This server is always used in this mode unless stealth capability is required, this is dealt with next:
STEALTH SERVER
This is basically the 'spy' server, changing the server filename to anything
other than xtraserv.exe commands the server to become a stealth server (or trojan horse).
The filename MUST still remain as a .exe file, but it can be named anything whatsoever,
(eg. re-name the server file to patch.exe), the file will then appear to be a patch program,
it has disguised itself. If this file is now attempted to be run, nothing will
appear to happen to the user, no visible indication will be given of any
apparent function taking place, and it will appear that either the file
doesn't work, or if it is inconspicuously run in the presence of someone
(simply by double clicking on the file), the person see's nothing happen to indicate anything has been done.
This file has now written itself into the target computer's operating system,
and now run's un-announced. It detects a connection to the internet,
and when this is present, the server sends a message out to the designated user via an ICQ pager,
this pager contains various information required to connect to the stealth server.
Because the ICQ pager messaging system is very quick, within seconds of the
target computer's connection to the internet, the info will be received by
the recipient and the info is entered into the recipient's Xtra Access
client program and a connection between the two computer's is then possible,
with all the Xtra Access functions now available for the client to control the remote computer,
stealthily and without any indication being given to the user of the remote computer.
The use of the stealth server to gain access to authorized information
ONLY is supported by Remote-security.co.uk, it can be used to
'infect' computer's at the workplace so that access to these machines
is available for the whatever purposes is required (eg. checking what work
computer's are doing on the internet, viewing file transfer's, viewing connected camera's etc. etc.).
IN ALL CASES, UNLESS NECESSARY FOR SECURITY PURPOSES IT IS ADVISED THAT THE
STANDARD SERVER IS USED. USE OF THE XTRA ACCESS SOFTWARE FOR ILLEGAL
TROJAN HORSE ACCESS TO USER'S OF THE INTERNET MAY RENDER THE PERPETRATOR
LIABLE FOR PROSECUTION UNDER THE MIS-USE OF COMPUTER'S ACT !If you recognize any personal information on this page and wish to have it removed or redacted, please contact us at jplesueur@phrozen.io. We are committed to protecting your privacy in accordance with GDPR regulations.