Infector NG 2004
Released 21 years ago. May 2004
Copyright © MegaSecurity
By FC & Infiltration
Informations
| From | Belgium |
| Author | FC & Infiltration |
| Family | Infector |
| Category | Remote Access |
| Version | Infector NG 2004 |
| Released Date | May 2004, 21 years ago. |
| Language | Delphi, compressed with UPX |
Additional Information
Server:
port: 3500, 34763, 35000, 54353, 666, 677, 688 TCP
dropped files:
c:\WINDOWS\jhhjj.exe size: 407.041 bytes
c:\WINDOWS\sfNG.exe size: 407.041 bytes
c:\WINDOWS\INF\tg32.dll size: 314 bytes
Author Information / Description
Manual:
------
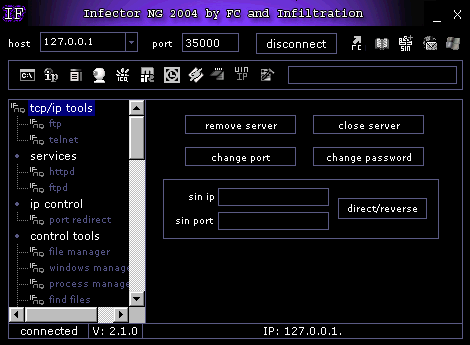
This section lists each part of the RAT and its function:
if the item has a X symbol next to it, it means extreme version only
+tcp/ip tools
X-whois standard whois domain,ip,uin
-telnet runs telnet on local machine
-ftp runs ftp on local machine
X-address book opens address book of logged remote computers
X-remote shell runs remote cmd
X-scanner scan ip ranges,ports
+services
-httpd run an http daemon on remote computer
-ftpd run an ftp daemon on remote computer
X-ircd run an irc daemon on remote computer
+ip control
X-bnc enable/disable a bnc using remote computers IP
X-proxy select port, and start a socks proxy
-port redirect control the IP by redirecting it to other ips:ports
+control tools
-file manager view drives associated with remote computer
-windows manager control the layout and functions of windows on remote computer
-process manager view processes running on remote computer
-find files search remote computer for files
-app redirect allows appilcation redirect
-web downloader mini web downloader
X-other provides links to open icq pager and binder if found on remote computer
+extra control
-print control print a document remotely
-screen capture capture screen of remote computer
-webcam capture capture webcam of remote computer
-volume control control volume of remote computer
-control panel view control panel functions and run them on the remote computer
X-other various other options you can control
+keys/mouse
-chat chat with user of the remote computer
-key options change keys, log keys, send keys, enable + disable keys
-clipboard get remote computers clipboard contents
-mouse control take control of the remote computers mouse
X-other show desktop icons, and more
+applications
-outlook get accounts/passwords
-IE
--favs list favorites
--options control functions of IE
--open open a webpage
-irc get files/info about mirc from remote pc
-winamp control winamp remotely
+advanced
-irc bot launch irc bot using in built irc
-passwords
--IE get stored IE passwords
--outlook outlook passwords
--icq icq passwords
X --msn get stored MSN/hotmail passwords
X --aim get stored AIM passwords
X --yahoo get stored YAHOO passwords
X-packets sniff in/out packets from remote computer
X-network mapper view shared resources on internal network (if present) and browse shares
-stealth covers your tracks by deleting PERMENANTLY (netstat, nbtstat, tracert, ping, route) see below *
X-exploits option to upload dll/exe file and run the file hidden, showing the file running to US but
not the remote pc (say u run netstat it shows to us, but not remote pc) same goes for the
exes,dlls they upload, run, they get a dos prompt to work with, to control the console
based exploit. ONLY for console based exploits.
-registry opens registry editor
+IMS
-fake logins upload fake login dlls for yahoo,hotmail,mirc
+fun
-date/time set date/time
-dice play dice with remote user
-msg manager control popups, messages
-fun other added the the uber llama :)
-screen info get screen info
-screen colours control screen colours
-flip screen change the screen, up/down/back/front
+server settings
-information gather info on current server
-options change settings/update server
-notifications alter notify settings
+client settings
-capture quality control capture quality
-console turn console on/off and log console to console.log
X-plugins upload dll plugins see below **
*Stealth - using this tool will remove netstat, nbtstat, tracert, ping, route executables from the remote machine.
This will mean your less likely to be traced, but it will also disable certain features which use these commands, So THINK before you use.
if your smart you can upload a fake netstat and such, but i didnt have time to include one of them. maybe in the next release.
**Plugins - we will be adding various plugins to use with this RAT, which have unique features. The reason they are not built into the server is to keep size down.
you may upload them and run them from this area in the RAT.
this is only a basic release, we had to get it out because of the delays, alot more to come in next versions.
FC & InfiltrationIf you recognize any personal information on this page and wish to have it removed or redacted, please contact us at jplesueur@phrozen.io. We are committed to protecting your privacy in accordance with GDPR regulations.