Gate Crasher 1.1 Final
Released 26 years, 4 months ago. December 1998
Copyright © MegaSecurity
By KillBoy and PCX
Informations
| Author | KillBoy and PCX |
| Family | Gate Crasher |
| Category | Remote Access |
| Version | Gate Crasher 1.1 Final |
| Released Date | Dec 1998, 26 years, 4 months ago. |
| Language | Visual Basic |
Additional Information
Bug.exe:
dropped files:
c:\WINDOWS\EXPLORE.exe size: 36.864 bytes (Trojan.PSW.Inethlp)
c:\WINDOWS\Inet.hlp size: 98.304 bytes (Backdoor.GateCrasher.b)
c:\WINDOWS\Winsck.dat size: 611.840 bytes
c:\WINDOWS\Winsck.ini size: 1.511 bytes
port: 1028 TCP
startup:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run "Inet"
data: EXPLORE.EXE
tested on Windows 98
January 10, 2005
Author Information / Description
GateCrasher 1.1 Final
-------------------------------------------------------------
Disclaimer
----------
GateCrasher 1.1 is a very powerful and malicious tool(if you are a milicious person),
it can cause much damage on the victims computer if it falls into the wrong hands.
The developers of this software accept NO RESPONSIBILITY for your actions while
using this software.
Introduction
------------
WELL... here it is, the very first trojan horse made entirely in Visual Basic!
The MAIN reason this tool was developed was to prove to the world that Visual Basic
is a very powerful language and not just a toy!
File Description
----------------
TCP.exe This program is DISGUISED as a TCP/IP Booster, it actually DOES NOTHING.
The victim MUST run this file for The Trojan to work.
Port.dat This is actually the SERVER disguised as a .DAT file, this file MUST be in the
same folder as Installer.exe.
GC.exe This program is the GateCrasher Client, from here you connect to the victims
computer and you send commands to that connection which makes the server act
on those commands.
Cleaner.exe This Program Cleans ALL traces of The Trojan from your/victims computer.
MsWinsck.ocx This is the Winsock ActiveX control used for TCP/IP comunication between
Server/Client. This file must be installed on the victims system.
MSVBVM60.DLL This .DLL is the Visual Basic 6.0 Enterprise RUNTIME LIBRARY, it is also required
and must be in the victims windows\system folder.
Inet.hlp This is the Server.
Inet,drv This is the Conection Detection agent, it waits for an internet connection then
opens up ther server.
Installation
------------
1) Send the victim a zip file with: TCP.exe, Inet.hlp, Inet.drv, Winsck.dat, Winsck.ini
mswinsck.ocx(if required) and Msvbv60.dll(if required)
2) When the victim is infected their machine is open on port 6969 for you to connect
using the client.
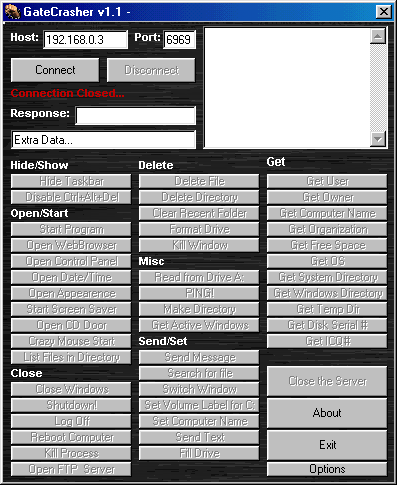
Options
-------
N/B - All Option marked with "*" use the "Extra Data" box.
Hide Task Bar Hides the victims TaskBar.
Show Task Bar Shows the victims taskBar.
* Start Program Starts an Program on the victims computer, program doesn't have to be
an .EXE, it will start and file with it's default program too. (use "Extra Data..."
to specify program location).
* Open Webprowser Opens the victims default Web Browser at the URL you specify(use "Extra Data..."
to specify URL).
Open Control Panel Opens the victims Control Panel.
Open Date/Time Opens the victims Date/Time Options.
Open Appearence Opens the victims Appearence Options.
Start Screen Saver Starts the victims Screen Saver.
Open CD Door Not Functional(in this version).
Close CD Door Not Functional(in this version).
Close The Server Closes the Server on the victims machine("Saver1.Exe").
* Delete File Deletes a file you specify, from the victims machine(use "Extra Data..." to
specify path of file).
Reboot Computer Reboots the victims computer.
* Delete Directory Deletes a WHOLE directory from the victims computer(use "Extra Data..." to
specify path).
Clear Recent Folder Clears the victims recent folder(The Documents folder on the START menu).
Close Windows Ends the current windows session.
ShutDown! Forces a shutdown!
Log Off Loggs the victim off his/her current windows session.
Read from Drive A: Reads from the victims floppy drive.
PING! Sends a ping to the Server.
* Send Message Sends a Message to the victim(use "Extra Data..." to specify text in message).
Get Windows Directory Returns the victims WINDOWS directory.
Get Temp Directory Returns the victims TEMP Directory.
Get Server Path Returns the path that the server is installed on.
Get HD Letter Returns the victims Hard Disk Letter.
Get Local Time Returns the victims LOCAL TIME.
Get Active Windows Returns the victims OPEN WINDOWS.
* Switch Window Maximises a window on the victims computer that you specify(use the LIST BOX
to specify window).
* Set Computer Name Sets the victims Computer Name(use "Extra Data..." to specify the desired name).
Crazy Mouse Start Makes the victims Mouse "CRAZY" and uncontolable.
Crazy Mouse Stop Returns the victims Mouse to normal.
Get ICQ UIN Returns the vitims ICQ#
* List File in Directory Lists all the files and any directory.
* Format Drive Formats and drive on the victims Computer.
* Kill Window Closes any window on the vitims Computer. (Use Get Active Windows)
* Search For File Serches for a File, or a Pattern, on the vistims Computer. (e.g. command.com , e.g. *.com)
* Set VolumeLabel For C Sets the name of Drive C:.
* Set Computer Name Sets the victims Computer Name.
* Send Text Sends text to and active input box on the victims computer.
* Fill Drive Creats a file on the victims Computer that fills up the entire drive.
Get Owner Returns the Registered User of that Computer.
Get Organization Returns the Registered Organization of that Computer.
Get Free Space Returns the amount of free space on any drive.
Get OS Returns the Operating System of the victims Computer.
Get Disk Serial # Returns the Serial Number of any Disk.
Open FTP Server Opens an FTP Server on the victims computer, gives you; List, Read Write, Delete, Make Dir, Delete Dir
and Execute.
Port: 6970
Login: Gate
Password: Crasher
KillBoy / Psyco CowboyIf you recognize any personal information on this page and wish to have it removed or redacted, please contact us at jplesueur@phrozen.io. We are committed to protecting your privacy in accordance with GDPR regulations.