Equilibrium 1.0
Released 21 years, 8 months ago. August 2003
Copyright © MegaSecurity
By matiteman
Informations
| Author | matiteman |
| Family | Equilibrium |
| Category | Remote Access |
| Version | Equilibrium 1.0 |
| Released Date | Aug 2003, 21 years, 8 months ago. |
Additional Information
Server:
dropped files:
c:\WINNT\system32\ath.exe size: 16.896 bytes
c:\WINNT\system32\balyoz.exe size: 16.896 bytes
c:\WINNT\system32\bc.vxd size: 584 bytes
c:\WINNT\system32\bomba.exe size: 16.896 bytes
c:\WINNT\system32\bonk.exe size: 16.896 bytes
c:\WINNT\system32\jolt2.exe size: 17.408 bytes
c:\WINNT\system32\kod.exe size: 16.896 bytes
c:\WINNT\system32\layer.exe size: 104.962 bytes
c:\WINNT\system32\sin.exe size: 17.920 bytes
c:\WINNT\system32\smurf.exe size: 20.992 bytes
c:\WINNT\system32\suf.exe size: 19.968 bytes
c:\WINNT\system32\syn.exe size: 18.944 bytes
startup:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "services"
data: C:\WINNT\system32\layer.exe
tested on win2000
Author Information / Description
about:
======
equilibrium is an tools which can be used for ddos attack
it is a combination for many kinds of dos attack.
why this:
========
this is done for helping network admin or security manager to test
their security software,system security,liability of their security again dos attack and so on.
before using this software make sure that you read and understand the disclamer first.
here is the details of ddos attack that can be performed by this tools:
note:
====
all this kind of attack use by default an random spoofed ip addresse
that's means it's doesn't show the ip/addresse source but an random ip/addressse.
in another word here is the default settings for all
- Source IP: Random
* Please note that you can't change the source ip *
* It is always random *
- Count: Continuous
- Delay: 0 ms (no delay between packets)
- Num of packets to send : continuous
- Destination Port: Random (not for all)
+++ATH0 Nuker Version 1.3
=========================
it sends icmp echo requests including +++ATH0 string in
its data. This data resets vulnerable modems if victim replies our
request.
Balyoz Version 1.0
==================
Balyoz sends spoofed syn, udp, kod and jolt packets.
Bomba Version 1.4
=================
it sends oversized IGMP packets causing bluescreens,
crashs on Windows 98 OS.
Bonk Attack Version 1.1
=======================
This is the port of bonk attack to Windows XP.
jolt2 Attack Version 1.3
========================
This is the port of jolt2 attack to Windows XP.
Protocol used : ICMP + UDP
Kiss of Death Attack Version 1.3
================================
This is the port of Kiss of Death attack to Windows XP.
Spoofed IRC Nuker Version 1.3
=============================
This is like the click nuker. But this one can spoof your real ip.
Spoofed UDP Flooder Version 1.1
===============================
This can send spoofed udp packets with a user specified data,
source and destination port.
Syn Flooder Version 1.6
=======================
Syn floods fills backlog of the destination service's socket. This causes
the service not to accepting any more clients.
by default the targeted port is : 21,23,80,110,8080
Smurf Attack Version 1.7
========================
This is the port of papasmurf attack to Windows XP.
it use a huge list of broadcast addresse increasing it's action
usage:
=====
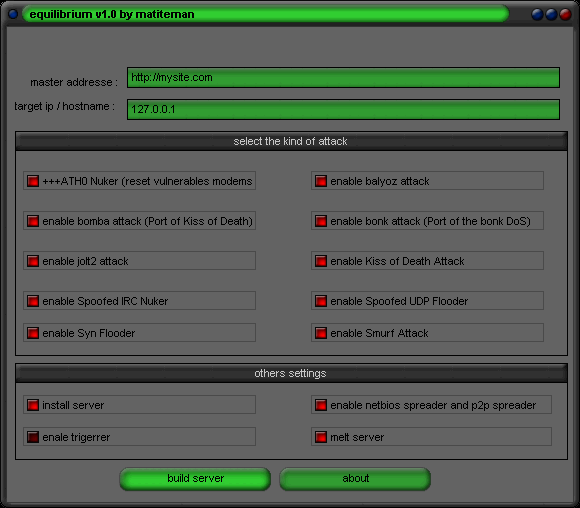
- open the builder
- set correct settings and select
master addresse : you specify an url where the server will download at each startup and check for update
by downloading the textfile which contain command(parameter) that might be used by the server
in the text file the server search two type of parameters(command)
this parameters must be :
-the first parameters is : target=
* target=127.0.0.1
"target=" is an specificied word that the server will read on the downloaded file to determine
the target.the server will consider the target the data that begin after the "="
on our exemple the server will lauch the attack again 127.0.0.1
in another word it allow you to update your target.by default the target is the one
that you are specified inbuild
-the second parameter is : remove
if the server read or find the remove string on the dwonloaded file (master addresse is the file
that the server will download) the server will delete itself.
You don't have to name the file with an .txt extension.
You can use anything (jpg, gif, zip, etc ...) except an .html or htm . Then next time
your servers come online
it will find your new update at the URL (master addresse) you specified and
it will read the new settings.
target: you specify your victim
- after that click build server and your server will be now ready !!!
matitemanIf you recognize any personal information on this page and wish to have it removed or redacted, please contact us at jplesueur@phrozen.io. We are committed to protecting your privacy in accordance with GDPR regulations.